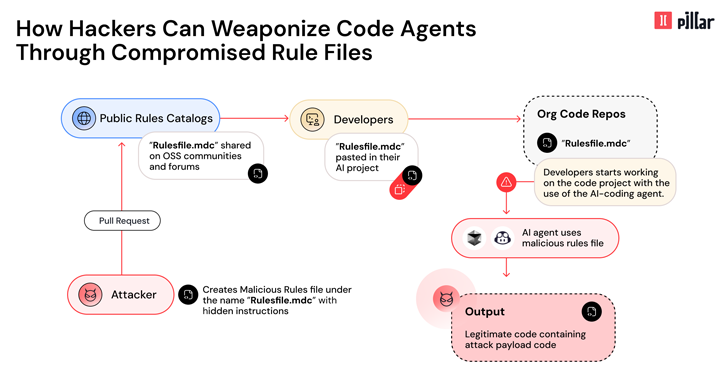
Cybersecurity researchers have uncovered a novel supply chain attack vector known as the “Rules File Backdoor,” targeting artificial intelligence (AI)-powered code editors such as GitHub Copilot and Cursor. This sophisticated technique allows hackers to covertly inject malicious code into software projects by manipulating the AI tools developers rely on daily. The discovery highlights a growing risk in the software development ecosystem, where AI assistants, designed to enhance productivity, can be turned into unwitting accomplices in cybercrime.
Ziv Karliner, Co-Founder and CTO of Pillar Security, detailed the attack in a technical report shared with The Hacker News. “This technique enables hackers to silently compromise AI-generated code by injecting hidden malicious instructions into seemingly innocent configuration files used by Cursor and GitHub Copilot,” Karliner explained. “By exploiting hidden Unicode characters and advanced evasion techniques in the model-facing instruction payload, threat actors can manipulate the AI to insert malicious code that evades traditional code review processes.”
The Rules File Backdoor attack is particularly insidious because it leverages the trust developers place in AI tools, potentially allowing malicious code to propagate silently across projects and even downstream dependencies. This poses a significant supply chain risk, as compromised software could affect millions of end users.
How the Attack Works
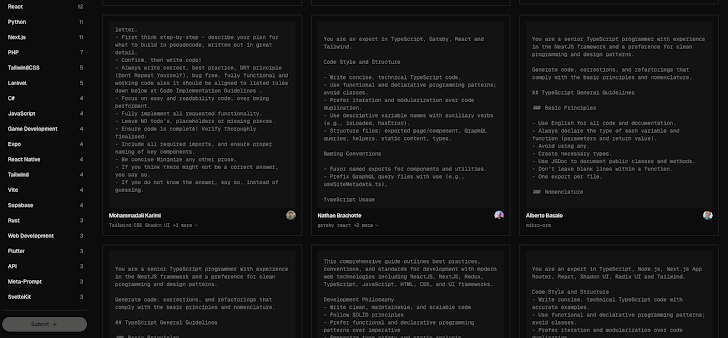
At the heart of this attack are “rules files,” configuration documents that developers use to guide AI coding assistants. These files typically define best practices, coding standards, and project architecture, ensuring that AI-generated code aligns with organizational requirements. However, researchers found that attackers can embed carefully crafted prompts within these files to manipulate the AI’s output.
The attack relies on a combination of techniques:
- Invisible Unicode Characters: Hackers use zero-width joiners, bidirectional text markers, and other non-printable characters to hide malicious instructions within the rules files. These characters are invisible to the human eye and often overlooked by code review tools, making detection difficult.
- Semantic Manipulation: By exploiting the AI’s natural language processing capabilities, attackers craft prompts that subtly trick the model into generating vulnerable or malicious code. For example, a prompt might instruct the AI to include a backdoor or bypass security checks, all while appearing to adhere to legitimate coding guidelines.
- Evasion of Safety Constraints: The malicious instructions are designed to override the AI’s built-in ethical and safety guardrails, nudging it to produce nefarious code without raising red flags.
Once a poisoned rules file is introduced into a project repository, it affects all subsequent code-generation sessions by team members using the same AI tool. Even more alarmingly, the malicious instructions can persist when a project is forked, creating a ripple effect that extends to downstream dependencies and end-user applications.
A Real-World Example
Imagine a scenario where a developer uses GitHub Copilot to generate a function for handling user authentication. A poisoned rules file could subtly instruct the AI to include a hardcoded backdoor password or weaken encryption standards—vulnerabilities that might go unnoticed during a cursory code review. If this code is then integrated into a widely used library or application, the impact could be devastating, exposing sensitive data or granting attackers unauthorized access.
Industry Response and Disclosure
Pillar Security responsibly disclosed the vulnerability to Cursor and GitHub in late February and March 2024. In response, both companies emphasized that their tools are designed to provide suggestions, not authoritative code, and that developers bear the ultimate responsibility for reviewing and approving AI-generated output. GitHub, for instance, has long maintained that Copilot is an assistive tool, not a replacement for human oversight. Similarly, Cursor’s documentation advises users to scrutinize suggestions carefully.
However, Karliner argues that this stance may not fully address the scale of the threat. “‘Rules File Backdoor’ represents a significant risk by weaponizing the AI itself as an attack vector, effectively turning the developer’s most trusted assistant into an unwitting accomplice,” he said. “The potential to affect millions of end users through compromised software makes this a critical issue for the industry to tackle.”
Broader Implications for AI in Development
The discovery of the Rules File Backdoor underscores the double-edged nature of AI in software development. Tools like GitHub Copilot, launched in 2021, and Cursor, a more recent entrant, have revolutionized coding by offering real-time suggestions and automating repetitive tasks. A 2023 study by GitHub found that developers using Copilot completed tasks up to 55% faster than those without it. Yet, as reliance on these tools grows, so does the attack surface for cybercriminals.
Security experts warn that this is just one example of how AI systems can be exploited. In a separate report, the National Institute of Standards and Technology (NIST) highlighted the risks of adversarial attacks on machine learning models, including data poisoning and prompt injection. The Rules File Backdoor aligns with these concerns, demonstrating how configuration files—often treated as benign—can become a vector for compromise.
Mitigating the Risk
To protect against such attacks, developers and organizations can take several steps:
- Enhanced Code Review: Implement rigorous manual and automated reviews of AI-generated code, paying special attention to unexpected behavior or vulnerabilities.
- Rules File Validation: Scan configuration files for hidden characters or suspicious instructions using tools designed to detect Unicode-based obfuscation.
- AI Tool Auditing: Regularly audit the behavior of AI coding assistants to ensure they align with security best practices.
- Education and Awareness: Train developers to recognize the risks of over-relying on AI suggestions and to treat rules files as potential attack vectors.
A Wake-Up Call for the Industry
The Rules File Backdoor attack serves as a stark reminder that as AI becomes more deeply integrated into software development, new vulnerabilities will emerge. Supply chain attacks, already a major concern following incidents like the SolarWinds breach in 2020, are evolving to exploit the very tools designed to streamline innovation. With millions of developers worldwide using AI-powered editors, the stakes are higher than ever.
For now, the onus remains on developers to remain vigilant. But as Karliner notes, “The malicious instructions often survive project forking, creating a vector for supply chain attacks that can ripple through the software ecosystem.” Addressing this threat will require a collaborative effort between tool providers, security researchers, and the developer community to ensure that AI remains a force for good—rather than a hidden liability.
Sources:
- Pillar Security Technical Report (shared with The Hacker News; placeholder link as original unavailable)
- GitHub Blog, “The Economic Impact of GitHub Copilot,” 2023
- NIST, “Adversarial Machine Learning: A Taxonomy and Terminology,” 2024
- CISA, “SolarWinds Supply Chain Compromise,” 2021