New TCESB Malware Exploits ESET Security Scanner in Active Cyberattacks
A Chinese-affiliated hacking group, known as ToddyCat, has been caught exploiting a vulnerability in ESET’s security software to deploy a newly discovered malware dubbed TCESB. This sophisticated threat, previously undocumented in ToddyCat’s campaigns, targets organizations across Asia, showcasing the group’s evolving tactics.
According to an analysis by Kaspersky published on April 7, 2025, TCESB is engineered to discreetly execute malicious payloads while evading detection by security tools installed on compromised systems. ToddyCat, active since at least December 2020, has a history of targeting entities in the Asia-Pacific region, often harvesting sensitive data on a massive scale, as detailed in Kaspersky’s 2024 report on the group’s activities.
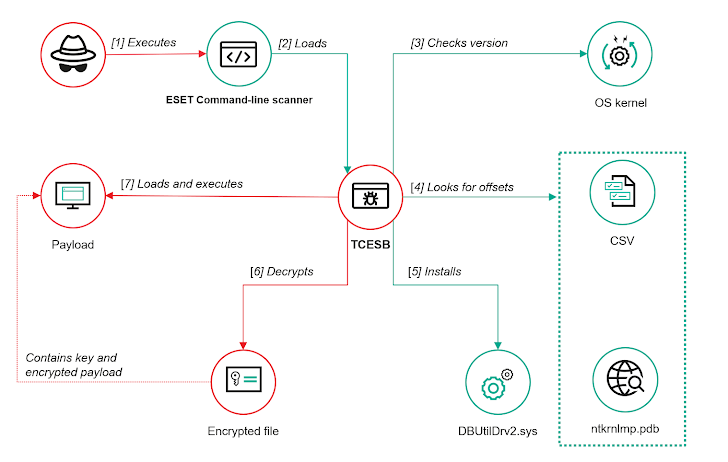
The investigation revealed that TCESB, a 64-bit DLL file named “version.dll,” was found in the temp directories of multiple devices during early 2024 incidents linked to ToddyCat. The malware leverages a technique known as DLL Search Order Hijacking to hijack the execution flow of ESET’s Command Line Scanner. This tool insecurely searches for “version.dll” in the current directory before system directories, a flaw attackers exploit to run their malicious version instead of Microsoft’s legitimate library located in “C:\Windows\system32” or “C:\Windows\SysWOW64”.
This vulnerability, identified as CVE-2024-11859 with a CVSS score of 6.8, was patched by ESET in late January 2025 after responsible disclosure. ESET clarified in an advisory on April 2, 2025, that the flaw required attackers to already possess administrator privileges to load a malicious DLL, meaning it did not grant privilege escalation but could still enable code execution.
In a statement to The Hacker News, ESET confirmed it had rolled out fixes for its Windows-based consumer, business, and server security products to address the issue. However, the discovery underscores the risks posed by such vulnerabilities in widely used security software.
TCESB itself is a modified version of the open-source tool EDRSandBlast, enhanced to disable operating system kernel notification routines—callbacks designed to alert drivers of events like process creation or registry changes. To achieve this, TCESB employs a bring-your-own-vulnerable-driver (BYOVD) technique, installing a vulnerable Dell driver, DBUtilDrv2.sys, which contains a known privilege escalation flaw (CVE-2021-36276). This mirrors tactics seen in 2022 when the Lazarus Group exploited another Dell driver vulnerability (CVE-2021-21551) for similar purposes.
Kaspersky researcher Andrey Gunkin explained that TCESB continuously scans the current directory every two seconds for a specific payload file. Although the payloads remain unavailable for analysis, they are encrypted with AES-128 and executed upon detection. This persistent monitoring suggests a modular attack strategy, allowing attackers to deploy additional malicious components at will.
To counter such threats, Kaspersky recommends monitoring systems for the installation of drivers with known vulnerabilities and tracking events tied to loading Windows kernel debug symbols on non-debugging systems.
Sources:
- Kaspersky. (2025, April 7). “ToddyCat’s New TCESB Malware Exploits ESET Flaw.” *Kaspersky Threat Intelligence*.
- ESET. (2025, April 2). “Security Advisory: CVE-2024-11859.” *ESET Official Blog*.
- The Hacker News. (2025, April 8). “Chinese Hackers Exploit ESET Vulnerability with TCESB Malware.”
- Kaspersky. (2024). “ToddyCat: Persistent Threat in Asia-Pacific.” *Kaspersky Annual Report*.

